What is Digital Experience (DX) ?
Digital experiences have become the cornerstone of just about every customer experience, driven in part by the rapid spread of customer activity among web, mobile, and social channels.The typical user experience has moved beyond desktop and laptop screens to an astonishing and growing array of mobile devices.
In the Oracle World, DX combines WebCenter, ADF including WC Sites, WC Content, WC Sites etc. DX Security should be a no-brainer at the end of this article.
Why do we need DX Security/Use Cases ?




References : I wished to summarize and set context using the following articles as source :
Security Architecture in the new Digital Experience Whitepaper (Oracle)
Enabling Secure Consumer Mobility (Kanishk Mahajan, Oracle Product Mgmt)
Digital experiences have become the cornerstone of just about every customer experience, driven in part by the rapid spread of customer activity among web, mobile, and social channels.The typical user experience has moved beyond desktop and laptop screens to an astonishing and growing array of mobile devices.
In the Oracle World, DX combines WebCenter, ADF including WC Sites, WC Content, WC Sites etc. DX Security should be a no-brainer at the end of this article.
Why do we need DX Security/Use Cases ?
- No defined network perimeter : Network Security spend more than 67% on network security. With digital economy demanding more collaboration and seamless user experience, new points of control need to be introduced : User identities, permissions/ access to IS etc. Cloud Computing and Mobile has further blurred network security.Sensitive data that was secured behind a robust enterprise firewall is now accessible via low-cost smart phones.

- Transformation of the perimeter : “Businesses now invest in security rather than spend on it. Security architects need to design security systems that complement business policies and processes.” - Chris Gavin, vice president, Information Security, Oracle.
- A “trust but verify” approach to both enable productivity and address security governance requirements. The objective is to establish one consistent security framework underlying all information systems. Because users and sensitive data are part of every transaction, identity management and database security are the common denominators of addressing most security requirements.

- Re-architecture of IT within organizations : Most services are being performed via software solutions that are architected in the cloud rather than on-premises requiring real-time exchange of accurate information. Organizations rely on identity management technology to facilitate dynamic trust relationships and support regulatory compliance requirements.
- Risk-Aware Architectures : Security architects are tasked with developing “risk-aware” architectures that factor in legal liabilities, the privacy of partner and customer data, and regulatory requirements. These security policies ensure that the organization is ready for internal and external audits.
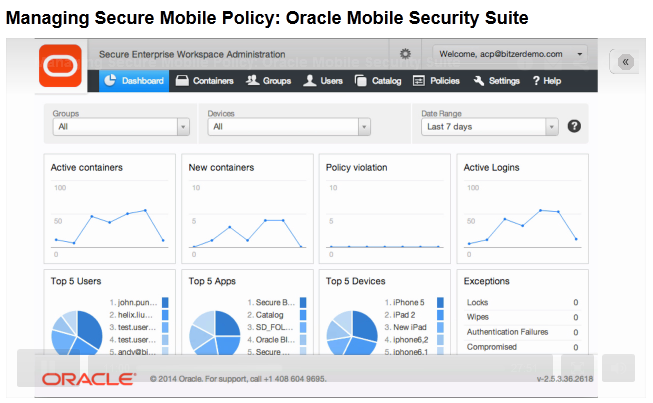
- Mobile Security :o By 2020, 80 percent of access to the enterprise will be via mobile devices and other non-PC devices, up from 5 percent today.o External providers will authenticate 60 percent of all users connecting with enterprises.o By 2020 there will be more than 50 billion IP-enabled devices in use around the world.


- Internet of things (IoT):According to Vadim Lander,
chief identity architect at Oracle, there are three types of security concerns
associated with the Internet of Things:
o Device Identityo Application Identityo User Identity
- Cloud Security : Customers that contract with cloud vendors need to be able to control the identity management process for external applications and on-premises apps via single-sign-on procedures. These solutions should also make it easy to provision and de-provision users and to extend entitlement credentials from on-premises applications to cloud applications. Such controls are even more important when securing databases. According to IDC, 66 percent of today’s most sensitive data resides in relational databases.
- Oracle Security Taxonomy as a measure of good security Design :Latency and consistency are two variables used to measure good security design. The objective is to reduce the latency of change and increase consistency across systems and applications. Oracle engineers hardware and software to work together. This cohesive approach reduces the latency of change and increases consistency. By embedding security technology into every layer of the technology stack and securing the integration between layers, Oracle not only delivers better performance with a smaller footprint, it also provides better security at a lower cost.
References : I wished to summarize and set context using the following articles as source :
Security Architecture in the new Digital Experience Whitepaper (Oracle)
Enabling Secure Consumer Mobility (Kanishk Mahajan, Oracle Product Mgmt)